Security: Page 23
-
Some hackers are getting lazy
Palo Alto Networks' Unit 42 found ransomware written by bad actors who failed "to make their lures appear legitimate in any way."
By Samantha Schwartz • April 14, 2020 -
Travelex paid the ransom, breach investigation still underway: report
After discovering the attack, the company took down its websites globally to contain the spread of the virus.
By Samantha Schwartz • April 9, 2020 -
 Explore the Trendline➔
Explore the Trendline➔
 Getty Images
Getty Images Trendline
TrendlineIT Security
Executives are working to improve the security posture of their businesses, a task that requires cross-function collaboration.
By CIO Dive staff -
Yes, developers break cloud security rules. But do companies have adequate policies in place?
Even though developers are circumventing compliance policies, companies struggle with adopting guidelines altogether.
By Samantha Schwartz • April 9, 2020 -
Coronavirus chaos ripe for hackers to exploit medical device vulnerabilities
As crowded hospital emergency rooms and ICUs in major U.S. cities try to keep up with demand for medical services, their networks face a rising threat level from cybercriminals probing for weaknesses.
By Greg Slabodkin • April 9, 2020 -
 Retrieved from Zoom on April 03, 2020
Retrieved from Zoom on April 03, 2020
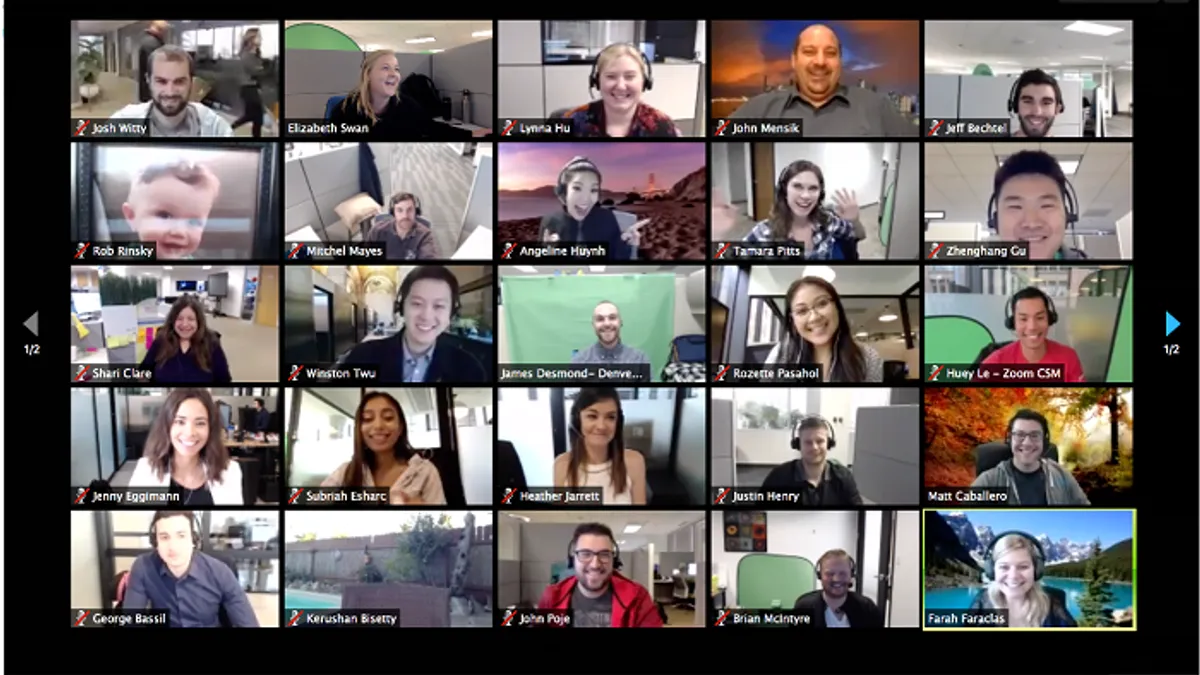
Zoom's no good, very rotten week: What's next in its security plans
It might be tempting to believe Zoom's flaws were intentionally hidden, it's more likely popularity brought scrutiny — something all prominent technologies eventually bear.
By Samantha Schwartz • April 9, 2020 -

 Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
FBI warns of a phishing uptick as hackers latch on to coronavirus
Bad actors are leveraging business email compromise schemes to target "municipalities purchasing protective equipment" and supplies related to the coronavirus response.
By Samantha Schwartz • April 8, 2020 -
Zoom's privacy woes lead back to end-to-end encryption
"We did not design the product with the foresight that, in a matter of weeks, every person in the world would suddenly be working, studying, and socializing from home," wrote CEO Eric Yuan.
By Samantha Schwartz • April 2, 2020 -
Sponsored by Coder
Keeping software development secure and productive in a work from home mandate
Many organizations have implemented remote work policies to protect their employees. As unexpected business disruptions emerge, Coder provides the solution software engineers need.
April 2, 2020 -

 "200323-Z-NI803-0587" by New Jersey National Guard is licensed under CC BY-ND 2.0
"200323-Z-NI803-0587" by New Jersey National Guard is licensed under CC BY-ND 2.0
Is coronavirus putting privacy on hold?
The pandemic creates a gray area between helping the greater good and loosening data privacy expectations.
By Samantha Schwartz • April 1, 2020 -

 Retrieved from Marriott on December 03, 2018
Retrieved from Marriott on December 03, 2018
Marriott International's latest data breach hits 5.2M guests
The hotel chain found the intrusion at the end of February and believes it began mid-January, according to the announcement.
By Samantha Schwartz • March 31, 2020 -
Coronavirus phishing attacks up 667% since February, research finds
Spring is typically the time of year bad actors send tax-related phishing emails, but this year they are leveraging human fear and health.
By Samantha Schwartz • March 26, 2020 -
Ransomware hits healthcare hardest, preys on SMBs
More attacks are moving past locking systems to breaching victims' data. And while restoring systems, targets may unintentionally wipe forensic evidence determining if data was stolen.
By Samantha Schwartz • March 25, 2020 -

 DESIGNECOLOGIST. [Photograph]. Retrieved from Unsplash.
DESIGNECOLOGIST. [Photograph]. Retrieved from Unsplash.
As Zoom meetings surge, beware digital gate-crashers
The security of a video conference call extends beyond keeping bad actors from crashing it.
By Samantha Schwartz • March 24, 2020 -

 National Institute of Allergy and Infectious Diseases. (2020). "Novel Coronavirus SARS-CoV-2" [Image]. Retrieved from https://www.flickr.com/photos/nihgov/49565892277/in/album-72157713108522106/.
National Institute of Allergy and Infectious Diseases. (2020). "Novel Coronavirus SARS-CoV-2" [Image]. Retrieved from https://www.flickr.com/photos/nihgov/49565892277/in/album-72157713108522106/.
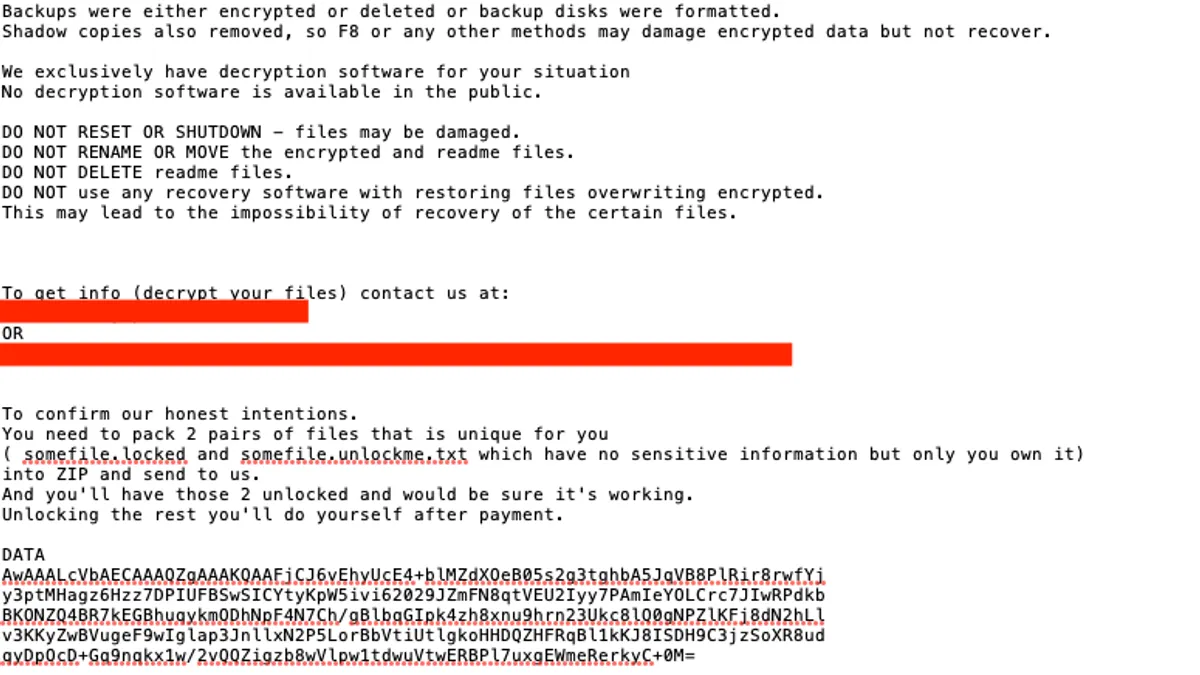
Report: Medical company set to aid coronavirus response struck by ransomware
A U.K.-based medical research firm discovered an attack and restored systems, but the attackers still published stolen data.
By Samantha Schwartz • March 23, 2020 -
Opinion
Everyone wants to be more secure — as long as it isn't an inconvenience
Apply that logic for CIOs and IT leaders, except the stumbling block revolves around revenue, or a lack thereof.
By Marc Mazur • March 19, 2020 -
2 cybersecurity considerations for a remote workforce
Companies that already have remote workers — whether a handful or a few thousand — know the associated risks.
By Samantha Schwartz • March 19, 2020 -
HHS suffers cyberattack as US deals with coronavirus response
The intent of the attack was to slow systems, though it was unsuccessful "in a meaningful way," according to the Bloomberg report.
By Samantha Schwartz • Updated March 16, 2020 -
Commission put out a 200-page guide for US cybersecurity: Here are 3 takeaways
The Cyberspace Solarium Commission spent a year analyzing how industry and government could work together to enhance cybersecurity. Will it make a difference?
By Samantha Schwartz • March 12, 2020 -

 Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Banks engage in self-hacks to keep defenses sharp
Enlisting teams of hackers to look for vulnerabilities helps banks take their security efforts beyond scanning software.
By Robert Freedman • March 11, 2020 -
Why the government says industry can't wait for a single cyber catastrophe
In its forthcoming report, the Cyberspace Solarium Commission consulted with the private sector to prioritize critical infrastructure in anticipation of a cyber Pearl Harbor.
By Samantha Schwartz • March 10, 2020 -

 Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Fragmented security patches prevailing issue for CIOs
Flaws force inventory management and security to meet at a crossroads. Inventory management is the foundation for maintaining security hygiene and without it, companies could prolong risk.
By Samantha Schwartz • March 6, 2020 -
Confidence in breach response low as privacy fines sink into companies
On average, organizations experienced seven breaches that required reporting under GDPR, according to research from Ponemon Institute and Experian.
By Samantha Schwartz • March 4, 2020 -
Boeing, Tesla manufacturer breached after ransomware attack
A ransomware attack hit Visser Precision, resulting in a breach of non-disclosure agreements and proprietary data, according to Brett Callow, threat analyst at Emsisoft.
By Samantha Schwartz • March 2, 2020 -
CISOs who leave after 2 years may not finish what they start
"Unless you sit in a role for an extended period of time, you don't know that the next transition is coming," said Dave Estlick, CISO of Chipotle.
By Samantha Schwartz • Feb. 27, 2020 -
Internal actors account for 30% of cyberattacks in manufacturing
Proper network segmentation can minimize the threat from internal actors by limiting access to applications or databases to specific employees.
By Matt Leonard • Feb. 26, 2020