Security: Page 3
-
Most enterprises can’t secure AI, Accenture says
Nearly 4 in 5 businesses lack the foundation needed to safeguard models, data pipelines and cloud infrastructure, the consultancy found.
By Lindsey Wilkinson • July 1, 2025 -
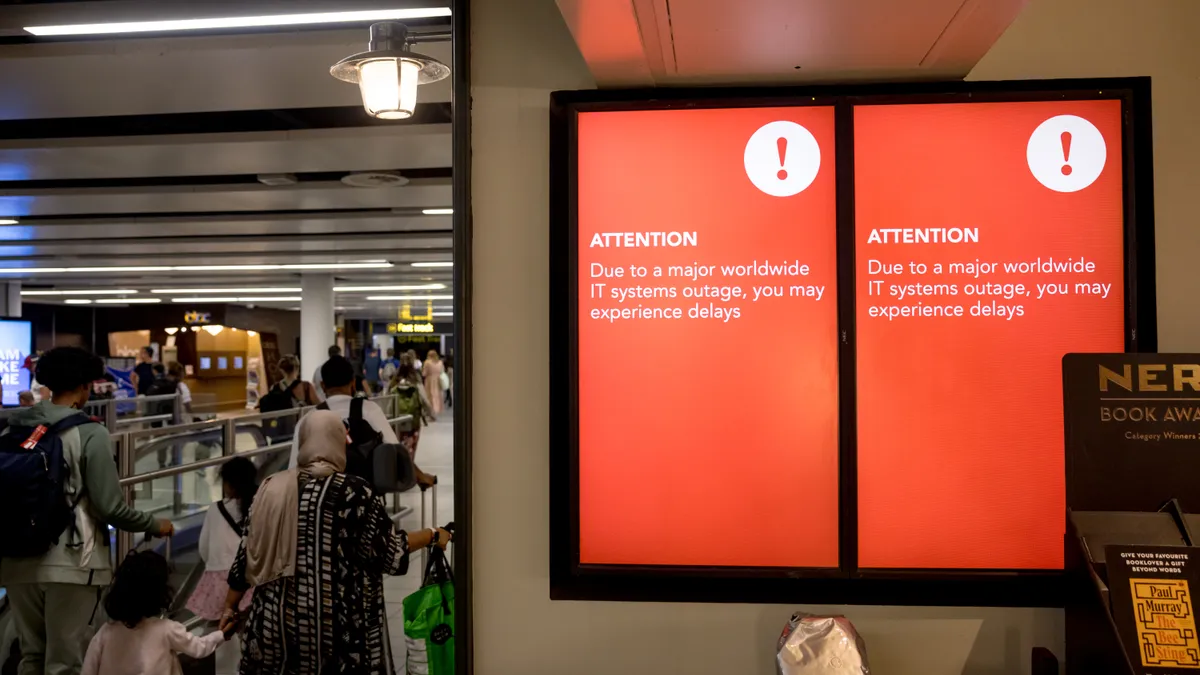
Microsoft to make Windows more resilient following 2024 CrowdStrike outage
The company has been working with security partners to make sure future software updates don’t lead to operational disruptions for customers.
By David Jones • Updated June 26, 2025 -
 Explore the Trendline➔
Explore the Trendline➔
 Getty Images
Getty Images Trendline
TrendlineIT Security
Executives are working to improve the security posture of their businesses, a task that requires cross-function collaboration.
By CIO Dive staff -
AI agents raise red flags for employees
Workers are concerned about unclear accountability when mistakes occur and a lack of human oversight, Boston Consulting Group found.
By Lindsey Wilkinson • June 27, 2025 -
Cloud storage buckets leaking secret data despite security improvements
More businesses are deploying identity protection services to shield privileged data, according to a Tenable report.
By Eric Geller • June 24, 2025 -
AWS CISO stumps for security as an AI enabler
AI's rapid development underscores the need for secure foundations, Amy Herzog said Tuesday during the company's annual cybersecurity conference.
By Roberto Torres • June 18, 2025 -
Cisco fortifies enterprise networking gear to support AI workloads
The company is aiming to help enterprises bolster security and resilience as they power up compute-intensive AI workloads.
By Matt Ashare • June 11, 2025 -
Trump scraps Biden software security, AI, post-quantum encryption efforts in new executive order
The White House accused the Biden administration of trying to “sneak problematic and distracting issues into cybersecurity policy.”
By Eric Geller • June 9, 2025 -
Microsoft, CrowdStrike, other cyber firms collaborate on threat actor taxonomy
After years of confusion, leading threat-intelligence companies will streamline how they name threat groups.
By David Jones • June 3, 2025 -
AI drives cyber strategies, security execs say
Basic vulnerabilities account for most cyberattacks, but security leaders say they’re more concerned about the risks of AI, Arctic Wolf research shows.
By Eric Geller • May 30, 2025 -
Home Depot elevates CIO from within as AI adoption plans progress
Angie Brown will lead technology strategy for the home improvement retail giant after a 27-year career with the company.
By Matt Ashare • May 30, 2025 -
How CIOs and CISOs can improve their collaboration
IT and security leaders best serve their organizations when there are clearly defined roles and mutual respect for their counterparts’ objectives.
By Jen A. Miller • May 28, 2025 -
Opinion
How to prevent AI agents from becoming data security threats
Agentic AI promises productivity boosts but could also create major security risks. For CIOs, relying on well-established governance policies could make the difference.
By Rahul Auradkar • May 20, 2025 -
Congress faces pressure to renew cyber information-sharing law
The law’s expiration in September could jeopardize information-sharing partnerships that have helped thwart cyberattacks in the U.S.
By Eric Geller • May 16, 2025 -
Generative AI may shoulder up to 40% of workload, some bank execs predict
Six in 10 bank executives list generative AI as a top investment priority this year, according to a survey published in April by KPMG.
By Caitlin Mullen • May 15, 2025 -
Sponsored by Tines
5 practical ways to drive security and IT team alignment
Could security and IT become your organization’s power couple? Here are 5 ways to make it happen.
May 12, 2025 -
Airlines in North America prioritize investments in cyber, AI
Spending plans come amid rising concerns over third-party cyber risk.
By David Jones • May 7, 2025 -
CIOs pay too much for not enough IT security
Cyber system complexity and a lack of adequate tools are adding to enterprise IT headaches, according to Logicalis Group.
By Nicole Laskowski • May 6, 2025 -
Sponsored by Snowflake
Achieving IL5: Empower mission success for the DOD
Deploy an end-to-end, fully managed & secure platform, from pilot initiatives to DOD-wide workloads.
By Matthew Rose, Director of Government Affairs, Snowflake • May 5, 2025 -
AI-fueled cybercrime may outpace traditional defenses
Defenders should begin using AI to counter cyber criminals’ adoption of the technology, according to security firm Check Point.
By Eric Geller • May 2, 2025 -
Google pours billions into AI, cyber and infrastructure expansion
The tech giant's cloud profits more than doubled year over year as it invested more than $17 billion, primarily in servers and data centers.
By Matt Ashare • April 25, 2025 -
AI impact on data breach outcomes remains ‘limited’: Verizon
While AI-generated text in malicious emails has doubled, the rate of successful phishing breaches is stable, according to a Wednesday report.
By Lindsey Wilkinson • April 23, 2025 -
Banks gear up to boost cybersecurity, cloud and data spending
In the race to scale generative AI capabilities, executives plan to increase foundational technology investments, according to Broadridge.
By Matt Ashare • April 21, 2025 -
Microsoft strengthens in-house cyber governance, training
As part of its Secure Future Initiative, Microsoft overhauled security practices following a series of crippling cyberattacks.
By David Jones • April 21, 2025 -
Bipartisan bill seeks extension to cyber threat info-sharing
Two federal lawmakers proposed a renewal of the Cybersecurity Information Sharing Act of 2015, which is due to expire in September.
By Elizabeth Montalbano, Contributing Reporter • April 18, 2025 -
Aviation sector faces rising cyber risks due to vulnerable software, aging tech
A report published Thursday called on federal authorities to conduct comprehensive risk assessments and take steps to modernize the air traffic control system.
By David Jones • April 15, 2025